I was the victim of $1500 in fraud that occurred through PayPal My Cash cards, a prepaid reloadable card produced by InComm. I have since found multiple other victims with thousands in more losses. I was then made victim again by InComm themselves via their fraud investigation team, which did nothing but victim blame me in the face of all evidence that I did nothing wrong, despite eventually providing evidence that proved they were at fault for everything. Skeet Rolling of InComm and its subsidiary ITC Financial Holdings leads this team and has been my primary contact and InComm decision maker, who has to this day continually denied all wrongdoing.
The problems with Skeet Rolling and InComm are the following:
- The PayPal My Cash cards (and likely other products) have a fatal security flaw. The secure PIN number for these cards is stored in plaintext in their internal database rather than encrypted. It furthermore does not even appear to be hidden with basic security privileges such as views. Short version: it’s easy to read, most anyone can read it, and it’s often worth $500.
- Employees are embezzling.
- I’ve been able to connect my loss to the specific employee who embezzled it.
- InComm supposedly uses some type of model to determine cases of Victim Assisted Fraud (VAF) – where someone is tricked into voluntarily giving up their secure PIN. However this model knowingly creates false positives – which InComm does not mind (or is even its intent) as they can deny assisting victims under the guise of investigation.
- Skeet Rolling still refused to restore my funds even with proof of everything above.
Excerpts from the below videos support these statements as follows;
1:25 – employees embezzling (in reference to $2500 loss from Jun L.)
An uncensored version of this video can be provided upon request:
6:00 – I tell you what the secure PIN will end with before I scratch off silvering to reveal it. This information has never been communicated out by InComm and their fraud team in Columbus, GA physically examined this exact card and found no evidence of tampering.
2:30 – I show InComm determined my card loss is a result from being a participant in VAF
8:40 – I begin tracing the email account associated with the PayPal address my money was loaded to (Brittany)
10:20 – Brittany’s friend Zach worked at InComm (quit shortly after my loss) as a DBA – the superuser for a database who could see the PINs even if protected – however they were not protected anyway (thus how I was able to reveal one before scratching off the silvering)
Surely there are more incidents of losses but one would only know the scope by investigating InComm’s own internal incident tracking database. To date, those that my story has found:
| Name | Amount |
|---|
| Mike T | $1500 |
| Liz D | $500 |
| James M | $500 |
| Jun L | $2500 |
| Total: | $5000 |
Timeline of events, further evidence, and discoveries:
4/6/15, 5/1/15 – Initial purchase of PayPal My Cash cards from CVS and Walgreens ($2500)
7/4/15 – 7/7/15 – Unauthorized redemption of 3 cards ($1500)
7/8/15 – Failed attempt to redeem the cards myself.
7/8/15 – 7/9/15 – InComm notified, all evidence provided as requested, cases #613368 and #614118.
7/10/15 – Police report filed with Lake County IL Sheriff’s Department – Waukegan, IL at InComm’s request. Note this is not typical behavior as is done when unauthorized transactions are discovered on debit or credit cards, however is standard behavior for InComm. Detective Werner advised that in these cases typically there is little that they can do, and that they do not have much computer expertise on staff.
10/8/15 – Computers were down and Detective Werner was getting ready to retire when original report filed. It did not appear any action was taken until I followed up with him at this date on his part, nor was any action taken by InComm.
10/14/15 – Detective Werner provided InComm requested information to identify my case.
10/19/15 – InComm provided information back to Detective Werner. Likely this is the exact same information a credible former employee contact provided me later.
11/2/15 – It appears by this date Detective Werner retired and a new detective Thomas Lex reached out to InComm to obtain redemption details. To my knowledge no additional advancement was ever made along this line. The only purpose of this investigation is to try to track down scammers who duped participant victims of VAF, then to try and recover some restitution for the victim. Since no VAF occurred at any point however, all criminal wrongdoing that actually existed were actions taken against InComm.
It should be noted that at all times I have been treated as a participant in VAF despite never having a story stating or implying that I was duped into voluntary providing my secure PIN. At this point I had been sitting at a loss of $1500, blamed the entire time for the loss, and basically been called a liar on my story.
12/8/15 – I published my first story on my travel blog of PayPal and InComm Scam and Fraud seeking other victims.
12/9/15 – After half a year with no meaningful results, I reached out to executives directly seeking help with my experience. I noted my background in computer science and also noted that as a libertarian, if I actually made the mistake of VAF, that I would lie in the bed I made. I was hoping for a chance to accomplish something constructively.
12/11/15 – John Williams gave me a call, as the lead investigator under Skeet Williams. He poorly articulated their VAF model which was clearly based on poor logic and assumptions from the outset. I noted this in an e-mail to execs and the fraud team and that if I did not see more progress I would begin filing formal complaints.
12/15/15 – I filed many complaints to private, state, and federal organizations and let them know. The first complaint to the Better Business Bureau against InComm is available to read here as case 27451505.
12/17/15 – Finally a response from the real decision maker – Skeet Rolling. Skeet described part of the logic and their “fact patterns” for determining VAF, including nothing that once a loaded PayPal account was flagged as participating in VAF than anything that touches it also becomes VAF. This would be valid in the case where the person who obtains the PIN is always and only the person that also loads the PIN, but is false in all other scenarios, such as a 3rd party launderer liquidating PINs, or truly any 3rd party loading the money at all. This logic poisons the well, and is likely the reason for falsely determining why myself and others are participants in VAF. As blatantly and obviously poor the design of plaintext secure PINs in the database were for everyone to see, this is just as blatantly wrong an assumption to make.
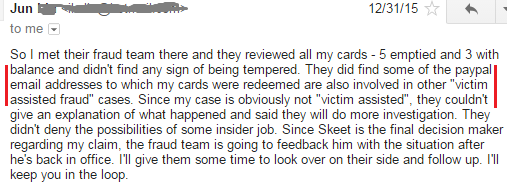
12/31/15 – A credible person with an InComm connection saw my story and thought I was too persistent to be making it up. I provided them with my 16 digit card numbers and they were able to tell me what the secure PINs were so I knew they were real. Further chatting revealed the PINs were not hidden from people that should not be able to see them, and furthermore, were stored in plaintext. They should be stored similar to passwords in an encrypted format, however they are essentially stored as a lit of $500 bills for anyone to easily dip their hand in to take. Up until this point I thought the worst fundamental computer mistake one could make was not encrypting a password, but this is far far worse. Note the product has been out since 2012!
12/31/15 – One of my fellow victims had cards where money was stolen but the silvering had not been scratched off, Jun L. Jun is local in Atlanta (InComm HQ) and made the trip out to Columbus, GA to show the cards to his team, who examined them in person. What did they find?
1/1/16 – My connection provided me the redemption details that were likely the exact same as those provided to law enforcement earlier noted above. I expected little as an intelligent launderer at this point probably used compromised accounts and/or fake accounts opened with stolen social security numbers. One address seemed fake, another real, neither of which I was able to do anything with. However the 3rd was associated with a babysitting account. I got stuck on a red herring trying to connect it initially to someone but it was a promising lead as the owner of that account lived in Atlanta, where InComm is headquartered.
1/17/16 – I got past my red herring and successfully traced my money. Via the babysitting profile, linkedin, and facebook, I was able to establish the money was loaded to Brittany W.’s account, and that she was friends with Zach G. on facebook, whom on linkedin was a former Database Administrator at InComm. Zach also took a new job around the time of the theft as well. Is Brittany W. an innocent intermediary? Due to not physically having the card yet still loading the money, and being identified as a VAF associated account even apparently before my incident, I am skeptical she is 100% innocent.

1/19/16 – The first video and a new call with Skeet takes place. Jun’s case alone is enough to show that not only is their VAF determination model logically flawed, but that it truly is incorrectly identifying real cases. This alone is sufficient evidence to stop using the model and to restore my funds. This same day, all of the above information was also provided to Skeet Rolling. My expected response to all of this was a serious apology, my funds returned, and a very sincere “thank you” – however Skeet’s response was more of a “fuck you” – InComm did not change their position whatsoever, still claimed I was a participant in VAF, and denied restoration of my funds.
1/25/16 – I began speaking with Difie and Andrew from fbfglaw.com, who agreed to represent me (and fellow victims) in a class action suit with me as class representative. I thought I was going to have to sue InComm in small claims in Georgia – although at this point happily had lawyers retained for free, willing to take them to Federal court.
3/11/16 – My lawyers sent out a demand letter demanding restitution for myself and fellow victims.
4/8/16 – InComm’s lawyers offered me a settlement, which I accepted. They previously gave me $500 in an attempt to get me to go away but not the remainder. I’m sure this was only offered at this point as it was cheaper than paying their lawyers to fight me even more.
5/8/16 – I returned to the US from Istanbul as I was out of the country.
5/16/16 – I cashed my check and published my story of InComm Fraud on my travel blog.
6/10/16 – Filed my Consumer Financial Protection Bureau (CFPB) case #160610-001202 with full details of the above.
6/23/16 – Skeet responded that there is no merit to the above claims. However the evidence is undeniable and there are no alternate explanations for the information revealed above. I am skeptical the company has protected the PINs to this day and confident they have not reviewed past cases where they falsely concluded there was VAF and denied victims of their funds while blaming them for their loss.
6/24/16 – Confirmation that passwords are stored in plaintext still today and any general user with database access can see them. The proper approach would be 1. encrypted PINs and 2. access only provided to machine application IDs, even to the encrypted version.
8/10/16 – My source advised secure PINs were still kept in plaintext. I’m also confident Skeet did not update his the broken fraud detection model which has provided multiple false positives as noted above. I decided the only option I had available left to me to try and correct these problems was getting the information to someone inside the company who could fix them.
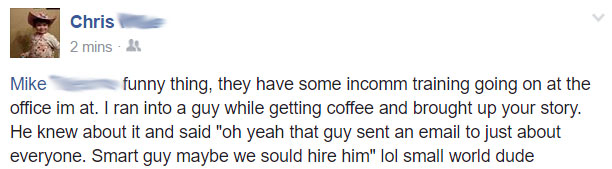
8/18/16 – Of the ~1800 or so InComm employees, I managed to e-mail over 550 of them. I did so using a combination of subjects, content, and source e-mails all over a span of 10 minutes so that they would have a difficult time stopping or removing the story as I sought to internally spread it around and reach someone who could and would actually address the problems. This included the entire executive suite. This site and videos within were provided. It was fun watching the google analytics live view and the hits roll in!
11/15/16 – A friend mentioned receiving some training from work from InComm where the 8/18 event was referenced!
2/1/17 – No one really got punished for the crimes of being criminals nor incompetent throughout this whole endeavor. If nothing else I will continue the public shaming on from Skeet Rolling and name the participants in this crime. I don’t know who took money from all the victims, but I know my money was loaded via PayPal to Brittany Washington and she is facebook friends with former InComm Database Administrator Zachary Graham. Both are from the Atlanta, Georgia area where InComm is headquartered.